The attacker can then, write and implement an exploit code while the vulnerability is still open and available. After the release of the exploit by the attacker, the developer acknowledges it and creates a patch to fix the problem. However, once a patch is written and used, the exploit is no longer called a zero-day exploit.
Windows 10 Zero-day exploit mitigations
Microsoft has managed to avert Zero-day Exploit Attacks by fighting with Exploit Mitigation and Layered Detection Techniques in Windows 10. Microsoft security teams over the years have been working extremely hard to address these attacks. Via its special tools like Windows Defender Application Guard, which provides a safe virtualized layer for the Microsoft Edge browser, and Windows Defender Advanced Threat Protection, a cloud-based service that identifies breaches using data from built-in Windows 10 sensors, it has managed to tighten the security framework on Windows platform and stop Exploits of newly discovered and even undisclosed vulnerabilities. Microsoft firmly believes, prevention is better than cure. As such it lays more emphasis on mitigation techniques and additional defensive layers that can keep cyber-attacks at bay while vulnerabilities are being fixed and patches are being deployed. Because it’s an accepted truth that finding vulnerabilities take a considerable amount of time and efforts and it is virtually impossible to find all of them. So, having above-mentioned security measures in place can help in preventing attacks based on zero-day exploits. Recent 2 kernel-level exploits, based on CVE-2016-7255 and CVE-2016-7256 are a case in point.
CVE-2016-7255 exploit: Win32k elevation of privilege
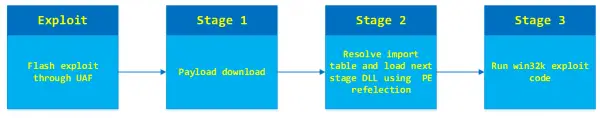
Last year, the STRONTIUM attack group launched a spear-phishing campaign targeting a small number of think tanks and nongovernmental organizations in the United States. The attack campaign used two zero-day vulnerabilities in Adobe Flash and the down-level Windows kernel to target a specific set of customers. They then leveraged the ‘type-confusion‘ vulnerability in win32k.sys (CVE-2016-7255) to gain elevated privileges. The vulnerability was originally identified by Google’s Threat Analysis Group. It was found customers using Microsoft Edge on Windows 10 Anniversary Update were safe from versions of this attack observed in the wild. To counter this threat, Microsoft coordinated with Google and Adobe to investigate this malicious campaign and to create a patch for down-level versions of Windows. Along these lines, patches for all versions of Windows were tested and released accordingly as the update later, publicly. A thorough investigation into the internals of the specific exploit for CVE-2016-7255 crafted by the attacker revealed how Microsoft’s mitigation techniques provided customers with preemptive protection from the exploit, even before the release of the specific update fixing the vulnerability. Modern exploits such as the above, rely on read-write (RW) primitives to achieve code execution or gain additional privileges. Here too, attackers acquired RW primitives by corrupting tagWND.strName kernel structure. By reverse engineering its code, Microsoft found that the Win32k exploit used by STRONTIUM in October 2016 reused the exact same method. The exploit, after the initial Win32k vulnerability, corrupted tagWND.strName structure and used SetWindowTextW to write arbitrary content anywhere in kernel memory. To mitigate the impact of the Win32k exploit and similar exploits, the Windows Offensive Security Research Team (OSR) introduced techniques in the Windows 10 Anniversary Update capable of preventing abusive use of tagWND.strName. The mitigation performed additional checks for the base and length fields making sure they are not usable for RW primitives.
CVE-2016-7256 exploit: Open type font elevation of privilege
In November 2016, unidentified actors were detected exploiting a flaw in the Windows Font library (CVE-2016-7256) to elevate privileges and install the Hankray back door – an implant to carry out attacks in low-volume in computers with older versions of Windows in South Korea.
It was discovered that the font samples on computers affected were specifically manipulated with hard coded addresses and data to reflect actual kernel memory layouts. The event indicated the likelihood that a secondary tool dynamically generated the exploit code at the time of infiltration. The secondary executable or script tool, which was not recovered, appeared to carry out the action of dropping the font exploit, calculating and preparing the hardcoded offsets needed to exploit the kernel API and the kernel structures on the targeted system. Updating the system from Windows 8 to Windows 10 Anniversary Update prevented the exploit code for CVE-2016-7256 to reach vulnerable code. The update managed to neutralize not only the specific exploits but also their exploit methods. Conclusion: Via layered detection and exploit mitigation, Microsoft successfully breaks exploit methods and closes entire classes of vulnerabilities. As a result, these mitigation techniques are significantly reducing attack instances that could be available to future zero-day exploits. Moreover, by delivering these mitigation techniques, Microsoft has forced attackers to find ways around new defense layers. For instance, now, even the simple tactical mitigation against popular RW primitives forces the exploit authors to spend more time and resources in finding new attack routes. Also, by moving font parsing code to an isolated container, the company has reduced the likelihood of font bugs being used as vectors for privilege escalation. Apart from techniques and solutions mentioned above, Windows 10 Anniversary Updates introduce many other mitigation techniques in core Windows components and the Microsoft Edge browser thereby safeguarding systems from the range of exploits identified as undisclosed vulnerabilities.