Sysmon System Monitor for Windows
The basic workflow behind System Monitor is that it stores information from Windows Event Collection (Event Viewer) and Security Information and Event Management (SIEM) agents like process IDs, GUIDs, SHA1, MD5 (SHA256) hash logs. It stores all these files under Applications and Services\logs\Microsoft\Windows\Sysmon\operational folder in Windows 10/8/7/Vista, and under System event log in older Windows operating systems like Windows XP.
How to install System Monitor
Download Sysmon [download link provided below]The downloaded file will be in zip format. Unzip the file using windows default file extractor or try Winrar, 7zip etc.Once the file is unzipped, run “Sysmon” accept the EULA and hit Next.Wait for System, Monitor to complete installation, that’s all!
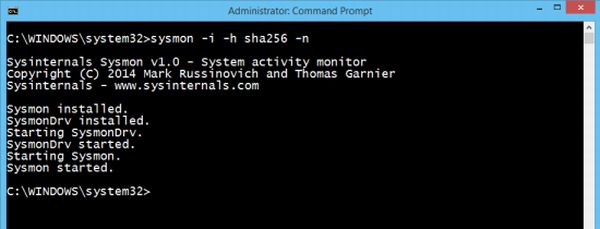
How to use Sysmon The command line in sysmon can be used to install, uninstall, check and to tweak System Monitor’s configuration: Few commands that user need to understand are: –i: install service and driver programs -n: stores network connection logs -u: uninstall service and driver programs -c: it updates the installed sysmon driver on the computer or helps to dump current configuration settings available -h: It specifies the algorithm applied to the program [by default SHA1 is applied] Examples:
To install the application with default settings: “sysmon -i accepteula” without quotes [SHA1 default]To install the application with MD5 [SHA256] settings: “sysmon -i accepteula –h md5 -n” To uninstall “sysmon -u”
System Monitor stores events like Event IDs as,
Event ID 1: Used for Process Creation,Event ID 2: A Process changed a file creation time with timestamp andEvent ID 3: For Network Connection.
The tool will keep running in the background and will write all event logs into a folder. After install or uninstall a system reboot is not all required. It is a must-have tool for all computers running on Windows. Go grab the System Monitor tool from here! UPDATE: Windows Sysinternals Sysmon now also records process activity to the Windows event log for use by incident detection and forensic analysis, includes driver load and image load events with signature information, configurable hashing algorithm reporting, flexible filters for including and excluding events, and support for supplying configuration via a configuration file instead of the command line. It also gets malware process tampering detection.